Vulnerabilities
5.0 Vulnerabilities
A vulnerability is a security flaw, glitch, or weakness found in software code that could be exploited by an attacker (threat source). The Vulnerabilities page lists all the vulnerabilities that are available in SW360. The Vulnerabilities are typically synced from SVM tools but can also be manually managed. They are listed independently without any relation to their linked projects/components/releases initially.
To open the Vulnerabilities page, click on the Vulnerabilities tab from the main menu.
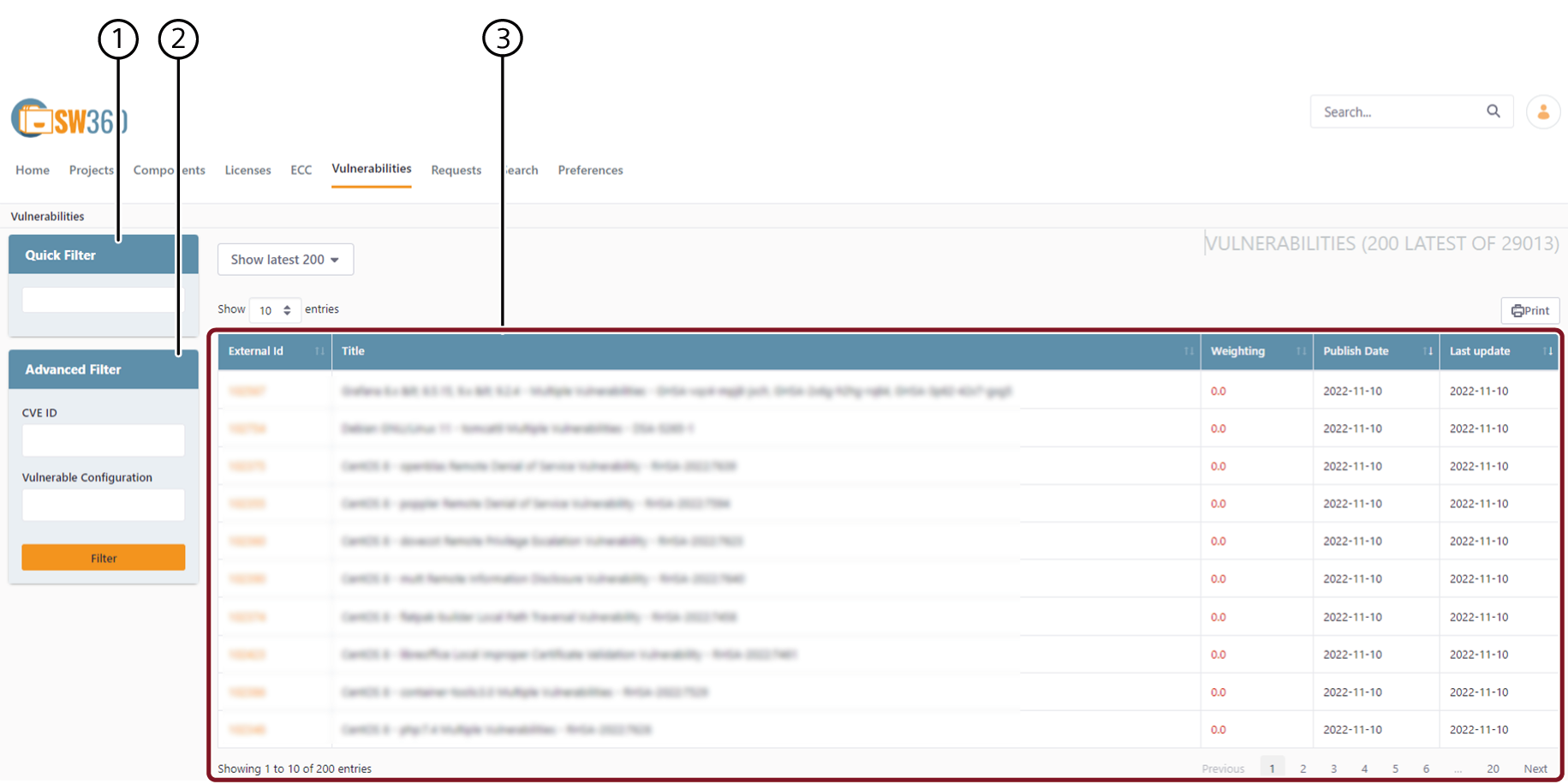
| Sl.No. | Description |
|---|---|
| 1 | Quick Filter |
| 2 | Advanced Filter |
| 3 | Vulnerabilities List |
5.1 Vulnerabilities List
On the Vulnerabilities page, you can view all the vulnerabilities that are available. The vulnerabilities are listed with the following information:
- External Id: The unique identifier for the vulnerability (e.g., CVE-2023-1234). Clicking this opens the detail view.
- Title: A brief title of the vulnerability.
- Weighting: Relevance or importance weighting.
- Publish date: The date the vulnerability was published.
- Last Update: The date the vulnerability was last updated in the system.
- Actions: Icons to Edit or Delete the vulnerability.
NOTE: USE ![]() TO SORT THE LIST ALPHABETICALLY OR IN ASCENDING/DESCENDING ORDER.
TO SORT THE LIST ALPHABETICALLY OR IN ASCENDING/DESCENDING ORDER.
5.2 Quick Filter
You can use the Quick Filter to search for a vulnerability by typing keywords. The list updates dynamically as you type.
5.3 Advanced Filter
The Advanced Filter dialogue box allows for more precise searching. To use it:
- Search by CVE ID (Common Vulnerabilities and Exposures).
- Search by Vulnerable Configuration.
- Click Filter to apply.
5.4 View Vulnerability
To open a view mode for a Vulnerability:
Search for the Vulnerability you want to view or navigate from the Vulnerability list and click on the External ID. When you click on External ID for a vulnerability you are displayed with the following information across tabs:
A. Summary
To view summary information for the vulnerability, click on Summary. You can now view:
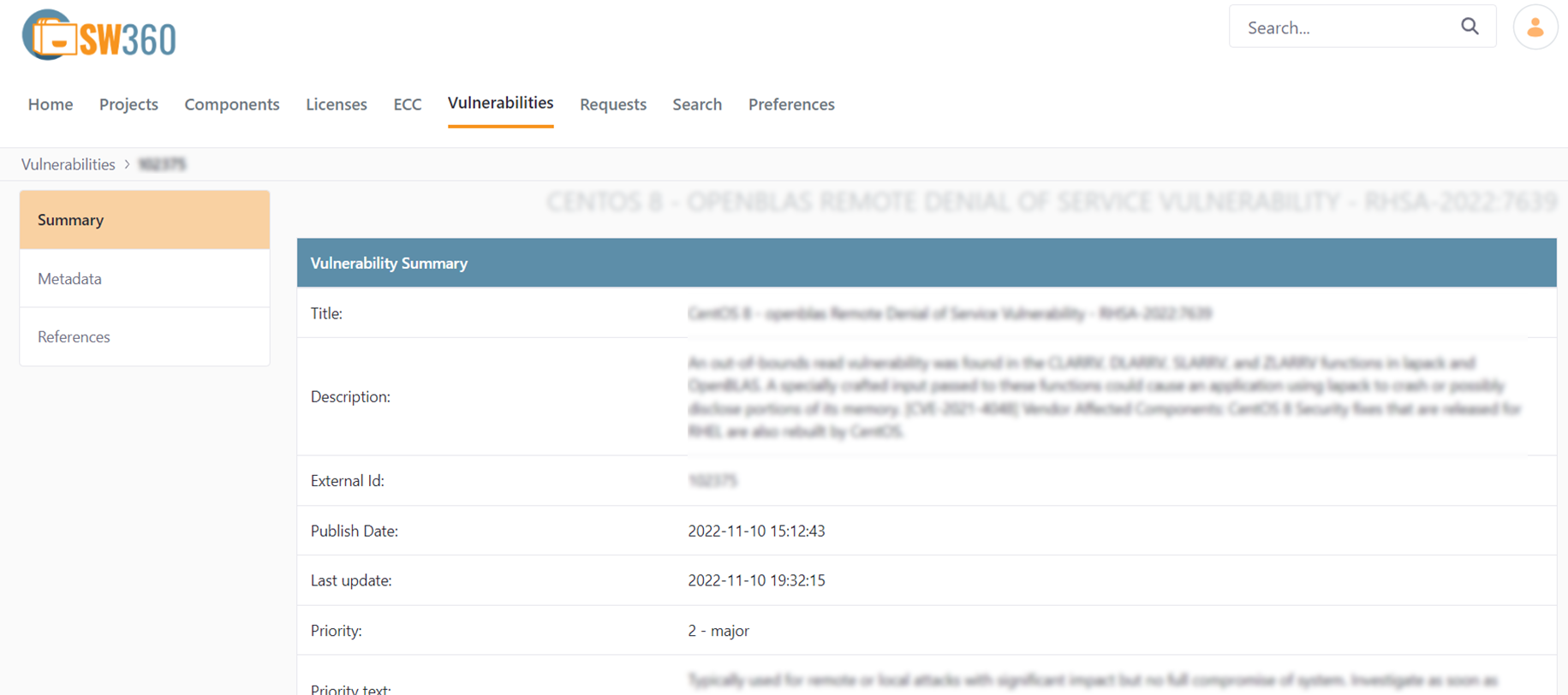
- Title: The title of the vulnerability.
- Description: Detailed description.
- External ID: The unique identifier.
- Publish/Last update date.
- Priority & Severity: Impact assessment.
- Legal notice: Source attribution.
- Linked releases: List of all the releases that the vulnerability is linked to.
B. Metadata
Displays additional metadata from the source if available (e.g., JSON dumps from the synchronization tool).
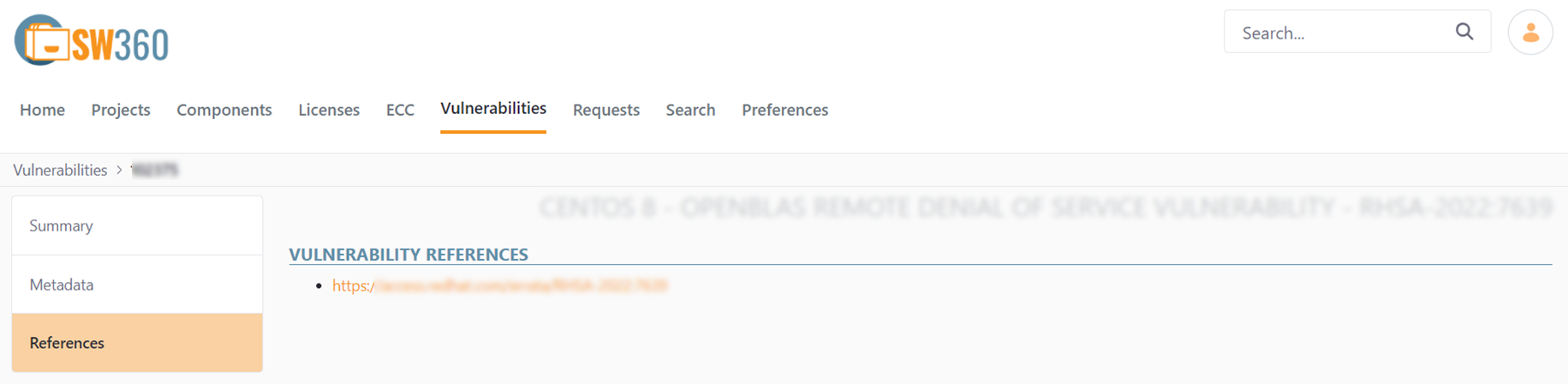
C. References
Lists all referenced websites and advisories.
5.5 Add Vulnerability
To add a new vulnerability manually:
- Click the Add Vulnerability button at the top of the main Vulnerabilities page.
- Fill in the Vulnerability Detail section:
- External ID (Required): Unique ID (e.g., CVE-XXXX-XXXX).
- Title, Description, Priority, Dates.
- CVSS Score: The Common Vulnerability Scoring System score.
- Fill in Vulnerability Impact: Availability, Confidentiality, Integrity levels.
- Fill in Vulnerability Access: Authentication, Complexity, Vector.
- Add References (optional):
- CVE References: Link related CVE years and numbers.
- Vendor Advisories: Links to vendor statements.
- Vulnerability Configurations: Key-value pairs for affected configurations.
- Click Create Vulnerability to save.
5.6 Edit Vulnerability
To edit an existing vulnerability:
- Navigate to the Vulnerability Details page (by clicking the External ID in the list).
- Click the Edit button.
- Modify the fields as needed (similar to the Add screen).
- Click Update Vulnerability to save changes.